The world’s most used penetration testing framework
Knowledge is power, especially when it’s shared. A collaboration between the open source community and Rapid7, Metasploit helps security teams do more than just verify vulnerabilities, manage security assessments, and improve security awareness; it empowers and arms defenders to always stay one step (or two) ahead of the game.
Penetration testing allows you to answer the question, “How can someone with malicious intent mess with my network?” Using pen-testing tools, white hats and DevSec professionals are able to probe networks and applications for flaws and vulnerabilities at any point along the production and deployment process by hacking the system.
One such penetration testing aid is the Metasploit Project. This Ruby-based open-source framework allows testing via command line alterations or GUI. It can also be extended through coding to act as an add-on that supports multiple languages.
What is the Metasploit Framework and How is it Used?
The Metasploit framework is a very powerful tool which can be used by cybercriminals as well as ethical hackers to probe systematic vulnerabilities on networks and servers. Because it’s an open-source framework, it can be easily customized and used with most operating systems.
With Metasploit, the pen testing team can use ready-made or custom code and introduce it into a network to probe for weak spots. As another flavor of threat hunting, once flaws are identified and documented, the information can be used to address systemic weaknesses and prioritize solutions.
A Brief History of Metasploit
The Metasploit Project was undertaken in 2003 by H.D. Moore for use as a Perl-based portable network tool, with assistance from core developer Matt Miller. It was fully converted to Ruby by 2007, and the license was acquired by Rapid7 in 2009, where it remains as part of the Boston-based company’s repertoire of IDS signature development and targeted remote exploit, fuzzing, anti-forensic, and evasion tools.
Portions of these other tools reside within the Metasploit framework, which is built into the Kali Linux OS. Rapid7 has also developed two proprietary OpenCore tools, Metasploit Pro, Metasploit Express.
This framework has become the go-to exploit development and mitigation tool. Prior to Metasploit, pen testers had to perform all probes manually by using a variety of tools that may or may not have supported the platform they were testing, writing their own code by hand, and introducing it onto networks manually. Remote testing was virtually unheard of, and that limited a security specialist’s reach to the local area and companies spending a fortune on in-house IT or security consultants.
BY
Jeff Petters JEFF PETTERS
UPDATED: 3/29/2020
Penetration testing allows you to answer the question, “How can someone with malicious intent mess with my network?” Using pen-testing tools, white hats and DevSec professionals are able to probe networks and applications for flaws and vulnerabilities at any point along the production and deployment process by hacking the system.
One such penetration testing aid is the Metasploit Project. This Ruby-based open-source framework allows testing via command line alterations or GUI. It can also be extended through coding to act as an add-on that supports multiple languages.
Get the Free Pen Testing Active Directory Environments EBook
“This really opened my eyes to AD security in a way defensive work never did.” What is the Metasploit Framework and How is it Used? The Metasploit framework is a very powerful tool which can be used by cybercriminals as well as ethical hackers to probe systematic vulnerabilities on networks and servers. Because it’s an open-source framework, it can be easily customized and used with most operating systems.
With Metasploit, the pen testing team can use ready-made or custom code and introduce it into a network to probe for weak spots. As another flavor of threat hunting, once flaws are identified and documented, the information can be used to address systemic weaknesses and prioritize solutions.
A Brief History of Metasploit The Metasploit Project was undertaken in 2003 by H.D. Moore for use as a Perl-based portable network tool, with assistance from core developer Matt Miller. It was fully converted to Ruby by 2007, and the license was acquired by Rapid7 in 2009, where it remains as part of the Boston-based company’s repertoire of IDS signature development and targeted remote exploit, fuzzing, anti-forensic, and evasion tools.
Portions of these other tools reside within the Metasploit framework, which is built into the Kali Linux OS. Rapid7 has also developed two proprietary OpenCore tools, Metasploit Pro, Metasploit Express.
This framework has become the go-to exploit development and mitigation tool. Prior to Metasploit, pen testers had to perform all probes manually by using a variety of tools that may or may not have supported the platform they were testing, writing their own code by hand, and introducing it onto networks manually. Remote testing was virtually unheard of, and that limited a security specialist’s reach to the local area and companies spending a fortune on in-house IT or security consultants.
Who Uses Metasploit?
Due to its wide range of applications and open-source availability, Metasploit is used by everyone from the evolving field of DevSecOps pros to hackers. It’s helpful to anyone who needs an easy to install, reliable tool that gets the job done regardless of which platform or language is used. The software is popular with hackers and widely available, which reinforces the need for security professionals to become familiar with the framework even if they don’t use it.
Metasploit now includes more than 1677 exploits organized over 25 platforms, including Android, PHP, Python, Java, Cisco, and more. The framework also carries nearly 500 payloads, some of which include:
- Command shell payloads that enable users to run scripts or random commands against a host
- Dynamic payloads that allow testers to generate unique payloads to evade antivirus software
- Meterpreter payloads that allow users to commandeer device monitors using VMC and to take over sessions or upload and download files
- Static payloads that enable port forwarding and communications between network
Metasploit Uses and Benefits
All you need to use Metasploit once it’s installed is to obtain information about the target either through port scanning, OS fingerprinting or using a vulnerability scanner to find a way into the network. Then, it’s just a simple matter of selecting an exploit and your payload. In this context, an exploit is a means of identifying a weakness in your choice of increasingly harder to defend networks or system and taking advantage of that flaw to gain entry.
The framework is constructed of various models and interfaces, which include msfconsole interactive curses, msfcli to alls msf functions from the terminal/cmd, the Armitag graphical Java tool that’s used to integrate with MSF, and the Metasploit Community Web Interface that supports remote pen testing.
White hat testers trying to locate or learn from black hats and hackers should be aware that they don’t typically roll out an announcement that they’re Metasploiting. This secretive bunch likes to operate through virtual private network tunnels to mask their IP address, and many use a dedicated VPS as well to avoid interruptions that commonly plague many shared hosting providers. These two privacy tools are also a good idea for white hats who intend to step into the world of exploits and pen testing with Metasploit.
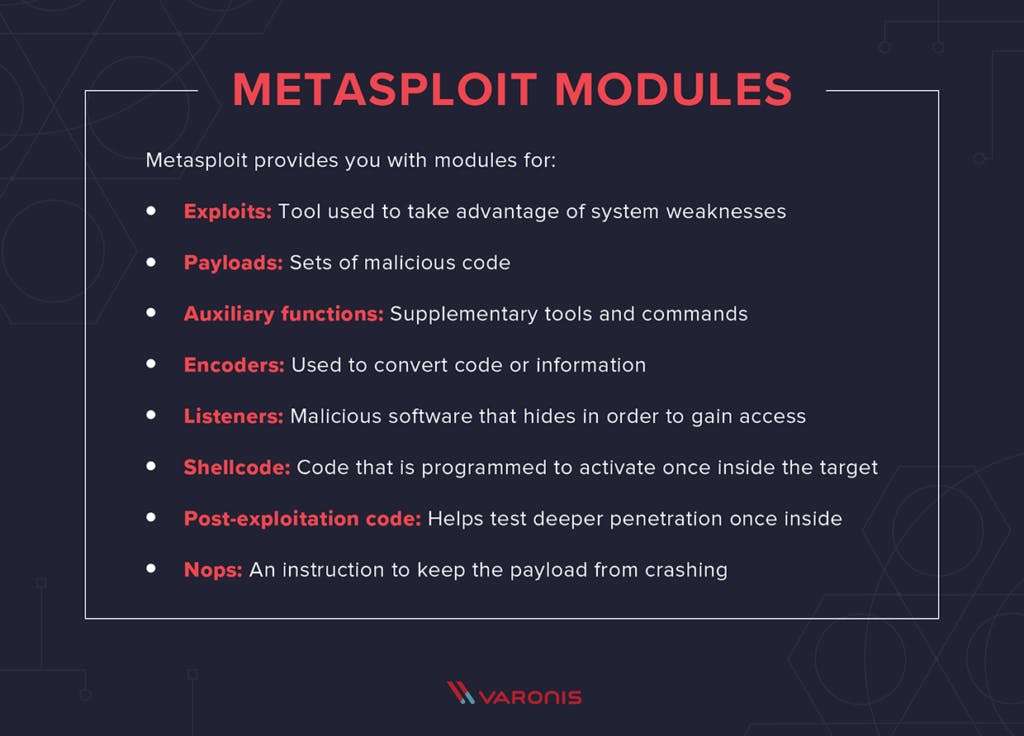
As mentioned above, Metasploit provides you with exploits, payloads, auxiliary functions, encoders, listeners, shellcode, post-exploitation code and nops.
You can obtain a Metasploit Pro Specialist Certification online to become a credentialed pen-tester. The passing score to obtain the certification is 80 percent, and the open book exam takes about two hours. It costs $195, and you can print your certificate out once you’re approved.
Prior to the exam, it’s recommended that you take the Metasploit training course and have proficiency or working knowledge
- Windows and Linux OS
- Network protocols
- Vulnerability management systems
- Basic pen testing concepts
Obtaining this credential is a desirable achievement for anyone who wants to become a marketable pen-tester or security analyst.
You can get metasploit by visiting thier official website
Join my TELEGRAM CHANNEL to learn how to use metasploit.
